Is there anything you can do to not be vulnerable to hackers? Yahoo is not as popular as it used to be, and maybe it’s because of the cyber attacks which have targeted the company and endangered its users. In this article, we’ll bring you information about the Yahoo cyber attacks and which measures we can take to enhance online security. Cashfloat is an online payday loans lender that helps educate people about saving money and personal finance. We hope you enjoy this article!
First, we’ll look at the Yahoo cyber attack in detail. We’ll explain who was responsible for the Yahoo cyber attack and how they did it. We will also examine which personal data hackers stole. How secure were Yahoo’s security measures? How did they react after the Yahoo cyber attack? Most importantly, we’ll explain how to recognise whether a hacker hacks your email account and what to do.
We conclude this report with lessons to learn in light of the Yahoo attack; how can we make our online defences as secure as possible to protect ourselves and our money.

- The Yahoo cyber attacks – who did it, how and why
- Which information did hackers steal from Yahoo accounts
- What were Yahoo’s security measures and how did Yahoo react to the Yahoo Cyber Attack
- How do you know if a hacker is hacking your Yahoo account and what should you do
- Internet security – passwords, security questions and how should you protect yourself and your money.
- What can you learn from the Yahoo cyber attack
The 3 Yahoo Cyber Attacks
- Yahoo Com Cyber-attack – September 2016
- Yahoo finance Cyber-attack – December 2016
- Yahoo mail login Cyber-attack – February 2017
Yahoo announced first details about the Yahoo cyber attack in September 2016. Hackers stole 500 million users’ data back in late 2014. Eight million of these accounts were UK accounts. Yahoo were aware of the intrusion but had not realised the extent of the breach. In July 2016; whilst investigating a separate data breach, Yahoo found information of 200 million customers’ accounts appear for sale on a darknet market site. The seller, with the nickname ‘Peace’, is believed to be a broker of information. They are also believed to be connected to data stolen previously from MySpace and LinkedIn.
Yahoo learnt about their second breach in November 2016. Law enforcement agents began sharing stolen data with the company. A hacker gave these details to the law enforcement agents. Hackers had allegedly seen small samples but had never seen the complete set of data. Yahoo did publicise this second Yahoo cyber attack; although later than the other one. Hackers attacked in August and took information from one billion users.
We know very few details about the third Yahoo cyber attack apart from the fact that hackers breached security in 2015-16. This more recent attack is not connected to the first two.
Who were the Yahoo Hackers?
Nobody knows for sure who the Yahoo hackers were. The private security company, InfoArmor, said that an elite group of hackers stole the Yahoo database. This is a group of hackers who hire out their services to the highest bidder. InfoArmor claims that the hacking team was ‘Group E’. They probably operate out of Eastern Europe, breached Yahoo and stole data for three private deals. Two of the three buyers are underground spammers while the third was a ‘state-sponsored actor’ interested in information on U.S government and military employees.
Yahoo has made no comment about this story although in December, their Chief Information Security Officer, Bob Lord said: “We have connected some of this activity to the same state-sponsored actor believed to be responsible for the Yahoo cyber attack data theft the company disclosed on September 22nd. 2016.”
Neither InfoArmor nor Yahoo has been more specific about which country/countries they believe to have paid the hackers for the information although there are rumours.
How were Yahoo login Emails Hacked?
Yahoo uses cookies to give users quick access to their username and password information without needing to re-enter it every time they log in on the site. However, people believe that the hackers gained access to the proprietary code and therefore were able to forge cookies. These cookies allow them to log into users’ accounts without even a password.

Which accounts did hackers access?
A Yahoo public statement in December said, “The investigation shows that the stolen information did not include stolen passwords in clear text, payment card details or bank account information. The company does not store payment card, and bank account information in the system the company believes was affected.”
If you read this and have a Yahoo account, you will probably breathe a sigh of relief. The stolen passwords were encrypted and the information had nothing to do with financial dealings and data. So you can stop panicking as there is nothing to worry about…or is there? Unfortunately, in the world of the internet, things are not quite as simple as that.
Yahoo Email Accounts – the Stolen Data
The data stolen was information from email accounts such as: names; phone numbers; dates-of-birth; passwords and email addresses. Encrypted and unencrypted security questions and answers were taken as well. This information seems harmless enough by itself but how can this information be used against you?
One of the problems is that the core security questions and answers have been called the weak link in your digital defences. Since many accounts ask the same questions, a hacker could use the information gleaned from a cyber-attack like the ones on Yahoo to conduct automated attacks called ‘credential stuffing’. They take the stolen data to build a program. This program tries to login to other online accounts with more sensitive information, such as online banking and shopping.
The same applies to passwords. Having to remember so many passwords means that many internet users use the same password for all their internet accounts. Unfortunately, when hackers breach one system or site, as was with Yahoo, all the other accounts are similarly compromised.
There are other dangers with a cyber-attack of this magnitude. Scammers use information to trick you into revealing other personal details like PIN numbers through ‘phishing’. This is usually done by email or by phone; scammers will know enough information about you to trick you into thinking you are talking to a representative of your bank, for example. On the pretext of checking your account details, people often unwittingly reveal details through an email or over the phone to an imposter. With this information, they are then able to access bank accounts and use your credit cards.
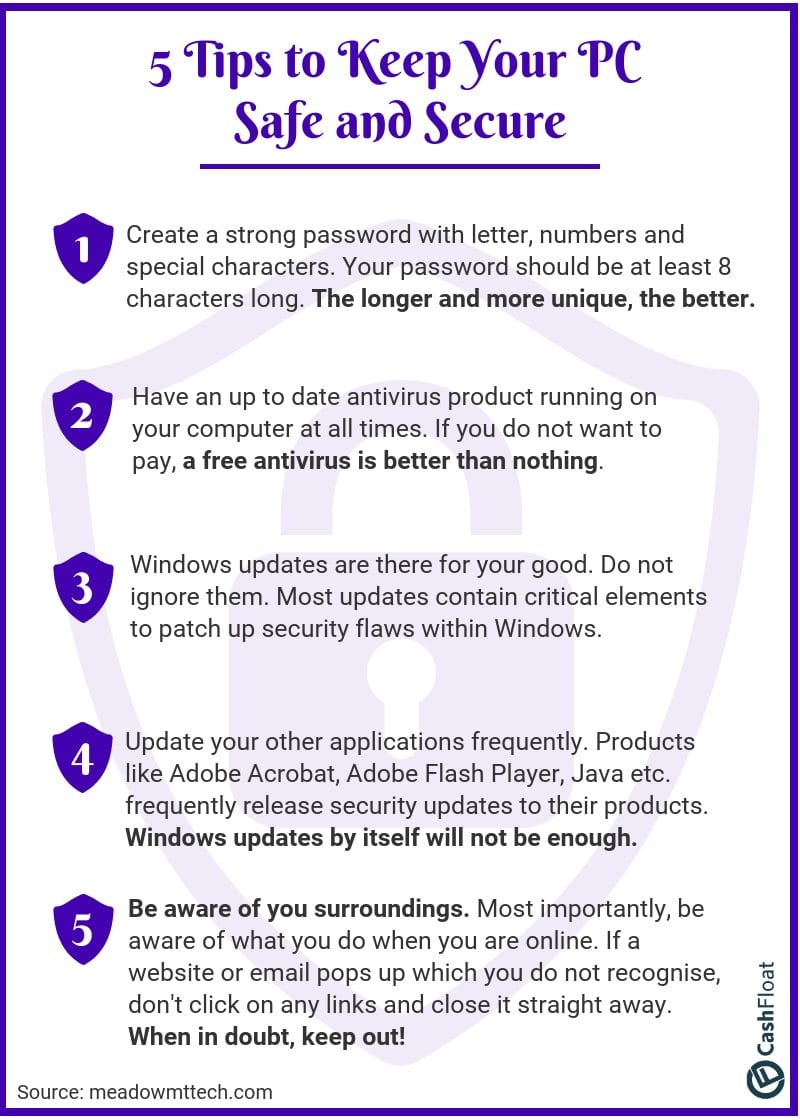
Click on the infographic to open as a PDF. Print it out and put in a prominent place next to your computer.
What Security Measures did Yahoo have in Place?
The majority of passwords on Yahoo were protected cryptographically with a hashing scheme. This is known as bcrypt. Its mathematical function is to convert plain-text passwords into a long string of text. This would be stored on the company’s servers. Security experts say this is safe as it slows down hackers. It prevents ‘brute force’ attacks, which is when they use a program to run through combinations of characters to crack a code. However, dates-of-birth are not usually encrypted in this way. This is because any site needs to access this kind of information as it is used for marketing and advertising purposes.
The other problem is that Yahoo accounts from before 2014 could have been protected by the MD5 algorithm, which has been proven to be vulnerable to brute force attacks.
Hackers take your details and pretend to be you in cases of identity theft. For example, to make use of credit facilities in your name such as loans. Victims of identity theft usually realise they are victims only when they have problems with their credit rating.
How did Yahoo react to the Attacks?
Since the cyberattacks, Yahoo have invalidated the forged cookies used in the security breach. They cannot be used again. Unencrypted security questions and answers cannot be used to access email accounts any more either. These have to be reset as well. Yahoo have also set up a 2-step verification process. A one-time security code is sent by text to the user’s mobile or generated by an application when someone logs in with the password. Without this code, the account cannot be accessed.
Despite this, some experts feel that Yahoo’s reaction has been a case of ‘Too little, too late’. Yahoo should be more pro-active to implement security. Hacking is the price we pay for the internet. There will always be people who want to pit their wits against security systems, whether for financial gain or not. Yahoo failed to protect their users. Some people in the field of internet security feel that Yahoo’s security system was massively underfunded.
There are also unanswered questions about when Yahoo found out about the attacks. Did it take them 2-3 years to fully understand the scale of the security breach? Or did they only come clean when law enforcement agencies became involved? And the other question is: if they are telling the truth about discovering the attacks, why did it take them so long to realise?
There was a significant change in Yahoo’s reaction to the seriousness of the cyber-attacks, and it is quite puzzling. In September, Yahoo ‘urged’ users to change their passwords. By December, Yahoo forced users to change their passwords. It ‘s hard to interpret their reasoning; were they trying to stop users panicking, or were they oblivious to the scale of the problem?
Do you have a Yahoo Account?
It probably seems an obvious question. You would know if you had a Yahoo email account. You would have Yahoo as part of the address. Did you know, however, that Yahoo also provides white-label email services to Internet Service Providers for BT and Sky in the UK?
Did you set up an account with Yahoo before August 2013? Maybe. Most probably, you have completely forgotten about it as you switched to another email service. If so, you could have had your personal information stolen. Yahoo estimates that it has 850 million monthly users and the other accounts are ‘dormant’. Now, if you think you were not affected, maybe think again.
How do I know if my Yahoo Account has been hacked?
- You have not received any emails.
- Yahoo Mail has been sending spam to your contacts.
- The information and settings on your Yahoo account have been changed.
- When you look at your recent activity page, you find logins from unknown locations.
Yahoo Email Account Hacked? What To Do
In light of these three security breaches in Yahoo accounts over the last six months, you have some questions to ask yourself. The first thing you must ask yourself is whether you wish to keep your email account with Yahoo. Do you trust Yahoo to protect your data?
If you decide to switch to a different email service, the process is quite easy. First, you open a new email account and then you import your email and contacts. You should immediately delete the old account. Dormant email accounts are a security liability. Even though you don;t use them, they contain personal information.
Email accounts user data remain on the company servers for about 90 days after you delete your account. Your provider may retain backups indefinitely.
Lessons learnt from Yahoo Attack
If you do not have a Yahoo account, you can still learn some lessons in the aftermath of these cyber-attacks. On this occasion Yahoo was vulnerable to a security breach but who knows which sites the hackers will turn their attention to next? In the light of this, how can you protect yourself and your financial dealings safe online? Of course, we trust sites to keep our data safe but there are still some common sense guidelines we should follow to make sure that we are protecting our personal information, and we are less likely to be victims of phishing or identity theft.
Protecting Yourself Online: Passwords
Your first line of defence is your password. Everyone knows that your password should never be something as simple as a row of numbers in order or the word ‘p-a-s-s-w-o-r-d’. But how can you choose a password?
Experts suggest that a password should be strong, long and unique. It should:
- Not be obvious (such as your mother’s maiden name).
- Be 12 or more characters including a mixture of capitals, numbers and punctuation symbols.
- Not contain sequences or repeat characters.
- Be different from passwords on other sites.
Some Yahoo users were particularly vulnerable due to their password practises. Every single online account should first of all have a separate password. Now, of course, it is easier to remember only one password but think about the cost to your online protection in case of a security breach.
If you find it difficult to remember each password, you can use a password manager platform like 1Password or LastPass. Password managers generate and store passwords and security answers for every account you have. You only have to remember a single ‘Master’ password. Alternatively, you can use the old-fashioned method of storing passwords on a piece of paper. Finally, do not forget to change your passwords regularly. If you’re not sure how to create a secure password, youc an use Lastpass’s free strong password generator.
Online Protection: Security Questions
Security questions and answers are your second line of defence in protecting yourself against hackers. Sites often ask the same questions. If one system is breached, all =your accounts are vulnerable. You should never use information that is in the public domain. For example, could hackers find out the information from any of your social media sites?
To protect yourself, you could use a password manager or. Or, you could invent different answers to your security questions for every site. If you think you will not be able to remember so many, you can make a note of them somewhere and keep them in a secure place.
Protection From Phishing & Identity Theft
One of the ways scammers find out your personal details is when you unwittingly give them the information.
Perhaps you will receive a phone call from the bank. The bank claims there is a security issue with one of your accounts. You should put the phone down on them and phone them back in 10 minutes, preferably from another device. Scammers can use a recording of their dialling tone to make you think they have hung up. When you call your bank’s number for verification, you are still talking to the scammers. You should never reveal details like your PIN number over the phone. In addition, you should never give any of your bank cards to a courier to ‘replace’ your card.
When it comes to email security, never click on links from unknown email addresses. The link might lead you to a site which looks like a facsimile of your bank. It will even have a matching logo for added deception. Often it is a bogus site which may get you to reveal sensitive banking data. The site can then pretend to be you and steal from your account and adopt your identity.
Aftermath of Yahoo Attacks
For Yahoo as a company, the future does not look bright. Initially, Yahoo was worth £125 billion at the height of the dotcom boom. Yet the cyber-attacks show how much Yahoo fell behind compared to Google and Facebook. Is the Yahoo name irreparably damaged? Will Verizon agree to takeover Yahoo, and will they modify or abandon their bid?
For Yahoo account users, many unanswered questions remain about the security breaches. Investigations of the U.S Securities and Exchange Commission may still bring unknown information to light. However, it is doubtful whether police will ever catch and punish the hackers. The Yahoo cyber-attacks have underlined once again how important internet security is. By following some simple guidelines, you can protect both you and your money.


